Private site authentication with JWT for SSO
One of the options for private knowledge base authentication is SSO (Single Sign On) via JWT (JSON Web Token), if you have a web application where users already login via other means.
Unlike our "Shared Password / Secret Link" option, this JWT authentication method requires a bit of coding on your site, however it provides better security since each user is authenticated with a unique individual token that can also expire as quickly as you'd like.
Users that you invite from the Team page will have access to your knowledge base if they login to their HelpSite account directly. You'll still need to use the Invite by Email method for Admins and Content Editors. However you can authenticate Read-Only users using this JWT method without first inviting those users in HelpSite or requiring them to create a password.
Please get in touch if you have any questions or issues using JWT authentication with HelpSite!
Enabling JWT authentication for your site
After clicking Save, scroll down and you'll be presented with the Secret Key (used in the code on your server, explained below) and an optional Login URL field.
If you provide a Login URL, HelpSite will redirect users there if they visit your knowledge base with a missing, invalid, or expired JWT.
Here's a sample (but the key shown here won't work for you).
Generate a JWT
Use jwt.io to learn about JSON Web Tokens, to help debug your implementation, and to find a library for your server-side programming language that you can use to generate the JWT.
Here are the fields that your JWT must have:
{
"iat": 1516239022,
"exp": 9999999999,
"aud": ["yoursubdomain"]
}Payload fields:
-
iat(Issued At) should be the timestamp you issue the token at. -
exp(Expiration Time) should be a timestamp set in the future. It will be rejected if it's in the past (more than 1 minute). Set this to a timestamp in the future – but only as far into the future you want users to have access before they have to reauthenticate on your own site. -
aud(Audience) should match your site's subdomain value as it appears on your site's Customizations > General page. It can be either a string or an array of strings, if you want to authenticate the user for multiple sites. For example, if your site's URL is typically "help.yourcompany.com" which points to "yoursubdomain.helpsite.com", you could use either "yoursubdomain" or ["yoursubdomain"] as the value for "aud".
Other important notes:
- Sign your token with the
HS256algorithm using the secret key from your site's Privacy settings page. - Keep your secret key secret! It should only appear in server-side languages (not in JavaScript that runs in user's browser). If it ever becomes compromised, see Retting a JWT Secret below.
Using a JWT
There are a couple options for how to pass the JWT to HelpSite to authenticate your users.
Pass via query string
You can pass the token via a jwt query string parameter, for example by linking users to your help site's URL.
If you're using a Custom Domain, that would look like:
https://help.yourcompany.com/?jwt=YOUR_JWT_HEREOr if you're just using a subdomain, that would look like:
https://yoursubdomain.helpsite.com/?jwt=YOUR_JWT_HERENotes:
- This URL can be used either in a simple hyperlink from your web app, or it can be used in an iframe.
- We will store the JWT in a permanent cookie so your users will be able to continue to navigate your help site. (To restrict how long a user can access your site after authenticating in this way, see the exp field mentioned above).
- You can link to individual article URLs – just append the
jwtquery string parameter to whatever page URL you want.
Set JWT in a cookie yourself
Alternatively, if you use a Custom Domain, you can set the JWT as the value of a cookie on your own domain and HelpSite can read it automatically without it needing to be passed via query string.
The cookie should have these characteristics:
- It should be set on the bare domain like
.yourdomain.com - Its name should be
helpsite_jwt - Its value should be the JWT as described earlier.
- It should be marked HttpOnly
- It should be marked Secure
- Expires is up to you, but you might just want to have a very far out expiration date (permanent cookie), since you should always use the exp field in the JWT to control token expiration regardless of what your cookie expiration is.
Resetting a JWT Secret
If you ever need to reset your JWT Secret (which will immediately cause existing JWT tokens to become invalid) then:
- Go to Customizations > Privacy, change the setting to "Visible to invited users only" (or any other setting besides JWT), and save the form. This will invalidate the existing JWT secret key.
- Then, choose the JWT option and save the form yet again. This will cause a new secret key to be generated and displayed.
Login URL
For knowledge base sites configured to use JWT authentication, you can provide us a Login URL that your users will be redirected to if they visit your knowledge base with a missing, invalid, or expired JWT. This helps provide a seamless experience for your users.
When HelpSite redirects users to your Login URL, we will append a query string parameter called jwt_error that will indicate the reason for the redirect. Values include:
- "missing" indicates no token was found in the user's query string or cookie.
- "expired" indicates the "exp" token field is not in the future.
- "aud" indicates the "aud" token field value is not valid for the given HelpSite URL.
- "iat" indicates the "iat" token field is not a valid timestamp in the past.
- "invalid" indicates some other issue with your JWT, and you should debug it on jwt.io.
Additionally, we'll include query string parameters expected_aud and from_url to help provide more context on what the user was attempting to access, and provide you the opportunity to redirect the user back to the same URL after authenticating.
If you have any trouble with JWT authentication on HelpSite, please get in touch!

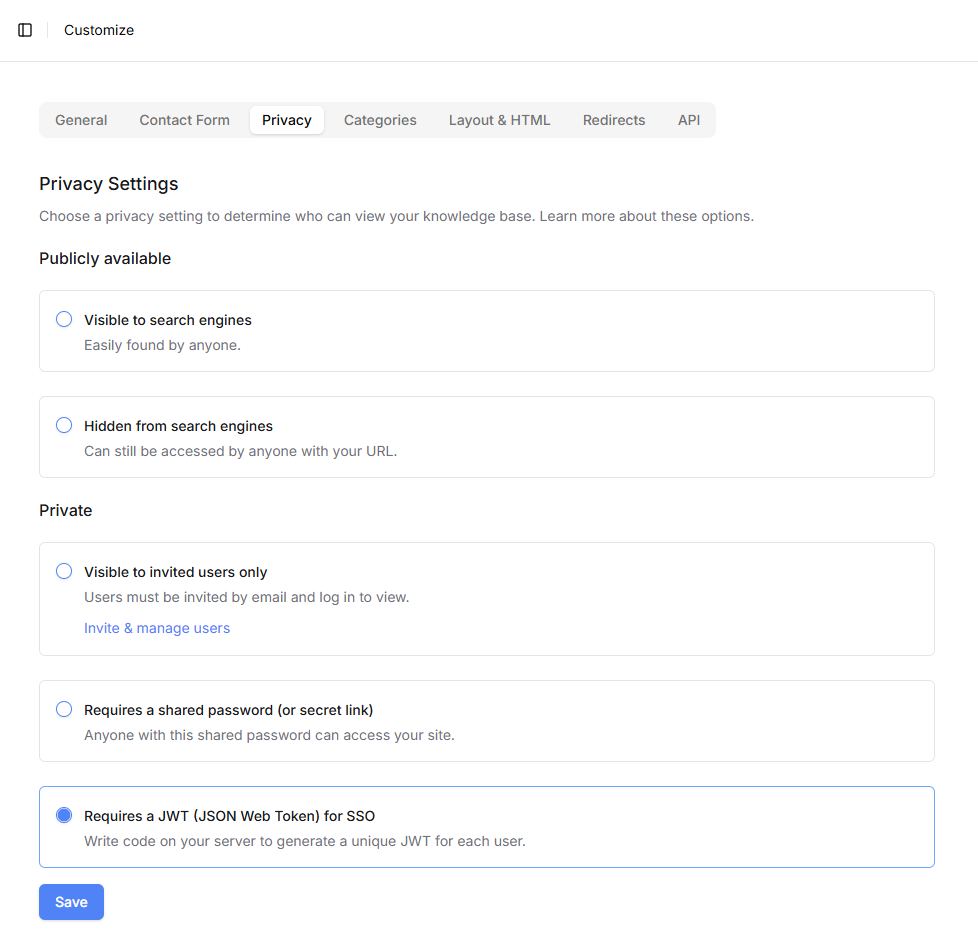 To get started with requiring JSON Web Tokens for authenticating your users, go to Settings > Customize > Privacy. Choose the "Requires a JWT" option and click "Save".
To get started with requiring JSON Web Tokens for authenticating your users, go to Settings > Customize > Privacy. Choose the "Requires a JWT" option and click "Save".